If you’ve read our guide to TLS, you’ll have encountered modern encryption algorithms like Advanced Encryption Standard (AES) and Rivest-Shamir-Adleman (RSA). These algorithms enable the symmetric vs. asymmetric encryption that underpins all SSL/TLS certificates used on the modern web, acting as the invisible shield that protects users and their data online.
But there’s another encryption algorithm you should know about: Elliptic Curve Cryptography (ECC).
In this article, we’ll explain what ECC is, the core concepts behind it, and the unique advantages it has.
What is Elliptic Curve Cryptography (ECC)?
Just like other systems of public key infrastructure (PKI), ECC uses a public and private key pair. What makes ECC different is how it generates these keys using the mathematics of elliptic curves.
Essentially, an elliptic curve is a type of graph that’s generated by a formula that is typically expressed as:
y² = x³ + ax + b
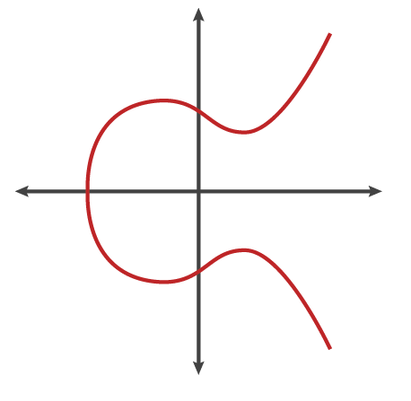
The equation describes a series of points that, when plotted on a graph, form a smooth and symmetrical curve.
Let’s break it down:
- You choose values for "a" and "b", which define the exact shape of the curve.
- Then, you plug in different x-values into the equation to calculate the corresponding y-values.
- Each (x, y) pair you get represents a point on the curve.
- When you plot all those points on a graph, they form a continuous, looping shape.
How does is Elliptic Curve Cryptography Benefit Encryption?
So, what’s the point of drawing a curvy shape on a graph? Well, this curve isn’t just nice to look at; it features special mathematical properties that make it incredibly useful for encryption.
One of the key features of elliptic curves is that you can perform predictable operations on the points that lie on the curve. For example, if you take two points on the curve and “add” them using a specific rule, you always get a third point that’s also on the curve. This allows you to repeat the operation over and over—combining a point with itself again and again—to generate new points in a way that grows exponentially.
So…how does this benefit encryption?
The secret to how ECC benefits encryption lies in something called scalar multiplication.
In the context of key-pair encryption, scalar multiplication is where you take a known starting point on the elliptic curve (called the generator point) and multiply it by a large, randomly chosen number (the private key) to get another point on the curve (the public key).
Here’s what it could look like in a very simplistic way:
- You choose a private key: a large random number (P).
- You multiply that number by the generator point (Q), and you get a public key: R = P + Q.
- The result, R, is the public key that can be safely shared.
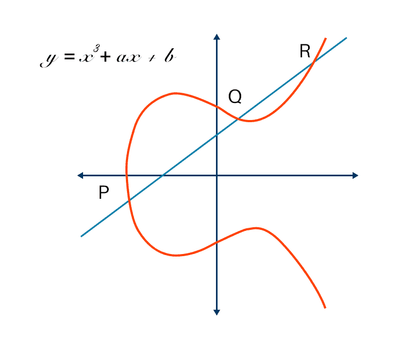
This helps to generate a secure key pair in such a way that it’s practically impossible to decrypt. While it’s easy to go from k to P using scalar multiplication, it’s practically impossible to go backwards and figure out the value of k.
This is very similar to hashing in that the scalar multiplication is a one-way function. It’s easy to go forward, not so easy to go back.
Why Smaller Key Sizes Matter — And How ECC Makes Them Possible
Aside from providing strong encryption through scalar multiplication, everyone loves Elliptic Curve Cryptography (ECC) because it offers enhanced security through much smaller key sizes than other methods like RSA.
What’s so great about smaller key sizes? Well, traditionally, a longer key size was a good thing because it meant there were more possible combinations to cycle through to break it, making them harder to brute force.
However, longer key sizes also require more computing power and memory to create, store, and process. As security needs and hardware have evolved, key sizes have gotten longer and longer.
If we compare the key size for 256-bit encryption between RSA and ECC, ECC wins out with a 512-bit public key size, compared to RSA’s bulky 15360-bit key size.
For SSL/TLS, smaller key sizes mean:
- Faster handshakes when loading websites
- Lower bandwidth usage
- Less storage needed (great when managing multiple certificates or keys)
With all these benefits, leading Certificate Authorities like DigiCert and Sectigo now offer ECC on all their SSL/TLS Certificates.
How Can You Get an ECC SSL/TLS Certificate?
Getting your hands on an ECC-enabled SSL/TLS Certificate is easy. All you need to do is select a compatible certificate and then specify ECC as the encryption algorithm when you generate your Certificate Signing Request (CSR).
At SSL Trust, when you compare our range of SSL Certificates, just go to “Product Specifications” and look at “Keys Supported” to see if the certificate supports ECC.
Conclusion: Encryption that Works Smarter, Not Harder
As computer hardware and decryption methods get more powerful and sophisticated, complex encryption methods like ECC become essential. While the rise of quantum computing will eventually pose a threat to ECC-based SSL/TLS certificates, they are the most powerful and reliable option available until Post-Quantum Cryptography becomes mainstream.
