In our earlier guide to TLS certificates, we provided a brief overview of symmetric vs asymmetric encryption and how they are used together in the critical handshaking process that takes place when you connect to a website secured with HTTPS.
In this article, we’ll dive a bit deeper into each encryption type, compare their strengths and weaknesses, and help you understand why they are both integral to secure online communication.
What is Symmetric Encryption?
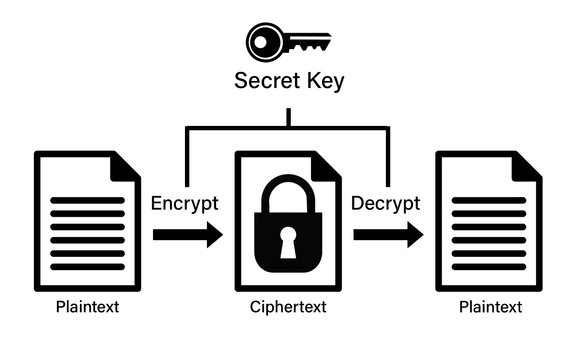
Symmetric encryption revolves around the use of a single secret key that both parties (the sender and receiver) must have to encrypt and then decrypt information (this is why it’s called “symmetric”).
Imagine placing a letter inside a lockbox and then locking it with a key. Once you mail the lockbox to your intended recipient, they will need an exact copy of your key to open it and read the message.
Here’s a breakdown of the process:
- Key Generation – A special secret key is generated that is only shared between the sender and recipient. This is a random, fixed-length string of numbers (typically either 128-bit or a more secure 256-bit string).
- Encryption – A symmetric encryption algorithm (like AES) converts the human-readable plaintext data into ciphertext using the secret key.
- Data Transmission/Storage – The encrypted message is either transmitted over a network or stored securely to be decrypted later within the same system.
- Decryption – The recipient uses the same secret key generated in the first step to unlock (decrypt) the message and view the human-readable plaintext.
The whole process is relatively simple – the real trick is that both parties must trust each other with the same private key before the information is sent.
This simplicity is the key advantage of symmetric encryption – it’s fast and allows for large volumes of data to be encrypted without using much processing power. This has made symmetric encryption ideal in performance-critical applications such as VPNs, real-time communication, and secure file storage for organisations.
However, this simplicity is a double-edged sword. Since it all relies on a single secret key, this key must be securely exchanged before any communication takes place, and if this key is intercepted, the entire system becomes compromised.
Block Ciphers vs. Stream Ciphers
One thing to understand about symmetric encryption is how different algorithms encrypt data differently. There are two main categories – block ciphers and stream ciphers.
Block ciphers encrypt data in fixed block sizes (typically 128 bits at a time). If the message exceeds the block size, it is split into multiple blocks, which are encrypted one at a time. Block ciphers are used in popular algorithms like AES and DES.
On the other hand, stream ciphers encrypt data in a continuous stream, doing it bit by bit. This method is used in algorithms like ChaCha20 and RC4.
So, which of these is better?
Well, similarly to our main topic of symmetric vs asymmetric encryption, it depends on what you’re trying to do.
While block ciphers are more well-studied and widely adopted amongst the cryptographic community, stream ciphers can be just as secure when implemented correctly.
In practice, block ciphers are more suited to encrypted, well-structured data, such as databases or secured communications after a key exchange (such as with SSL/TLS Certificates).
Alternatively, stream ciphers (as the name implies) are more suited to real-time data encryption, such as with voice/video calls, messaging apps, VPNS, or IoT devices with limited processing power.
So, one’s a little more heavy-duty, and one’s sleeker and more lightweight.
What is Asymmetric Encryption?
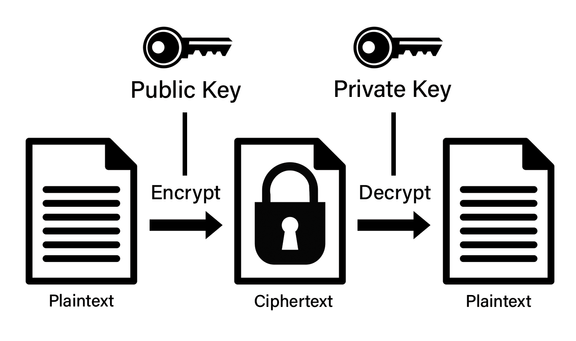
The inherent weakness of symmetric encryption (relying on a single key) is what asymmetric encryption corrects. With asymmetric encryption, you have a pair of keys where one is openly distributed and the other is kept secret.
This key-pair model forms the basis of Public-Key Infrastructure (PKI), which underpins all SSL/TLS Certificates.
Let’s use the same lockbox analogy. With asymmetric encryption, you would lock the letter inside the lockbox using your recipient’s public key, which anyone can learn about and have a copy of. This is a key associated with your recipient that they give to anyone who wants to send them a secure message.
After the lockbox arrives in the mail, they need to use a different key (the private key) to unlock it and read the letter. Even you, the sender, would be unable to open the lockbox after you locked it, since you don’t have that specific private key.
This solves the key weakness of symmetric encryption; you don’t need to find a way to securely share a single private key ahead of time (which risks being exposed).
Here’s a summary of the process so you can see where it differs from symmetric encryption:
- Key Pair Generation - Rather than generating a single private key, each party generates a pair of keys (one public, one private).
- Encryption – The data is encrypted with the recipient’s public key. Note that this public key does not reveal any useful info about the private key, so it’s safe to share openly.
- Decryption – The recipient then uses their unique private key to decrypt the message.
This one-way relationship makes asymmetric encryption highly secure, which is why it’s used with SSL/TLS Certificates. Additionally, this key-pair system is also useful for identity verification with S/MIME Certificates and Application-Signing Certificates.
The main downside to asymmetric encryption is that, due to the increased complexity, this encryption method is much more resource-intensive than symmetric encryption.
For example, let’s take the two leading asymmetric algorithms, Rivest-Shamir-Adleman (RSA) and Elliptic Curve Cryptography (ECC).
RSA uses operations based on the factorisation of large prime numbers. This involves modular exponentiation with very large integers (often 2048 bits or more). ECC relies on elliptic curve point multiplication, a form of repeated addition over a finite field, which is also quite computationally intensive.
While ECC is gaining popularity for being more resource-efficient than older methods like RSA, both still require a much higher degree of computational power when compared to the algorithms used in symmetric encryption, like AES.
So – Which Method is Better?
While this may sound like a cop-out, which is better really depends on the situation.
The core difference between symmetric and asymmetric encryption boils down to speed vs strength.
Asymmetric encryption is ultimately the stronger of the two when it comes to protecting data from prying eyes. However, due to its complexity, it’s unsuitable for mainstream use in a world where high-speed communication is expected and required.
This is why modern SSL/TLS Certificates use both encryption algorithms to secure online communications.
Basically, symmetric encryption is used for the encryption of the physical data, while asymmetric encryption is used during the handshake phase to securely exchange keys and verify identities. This hybrid approach provides the best of both worlds. You get strong security without compromising on performance.
So, instead of asking which method is universally better, it’s more practical to ask which method is best for the task at hand.
- If you’re encrypting large volumes of data quickly, symmetric encryption is your friend.
- If you need to establish secure communication between untrusted parties or verify identity, asymmetric encryption wins out.
In most modern applications, especially SSL/TLS, the best solution is to use both strengths to compensate for their individual shortcomings.
Conclusion: Stronger Together
In the world of SSL/TLS, symmetric and asymmetric encryption are not competitors; they’re two sides of the same coin. Working hand in hand, these encryption methods form the foundation of secure online communication, protecting everything from web traffic to emails, financial data, and much more.
